Discuss the machine reference model of execution virtualization.
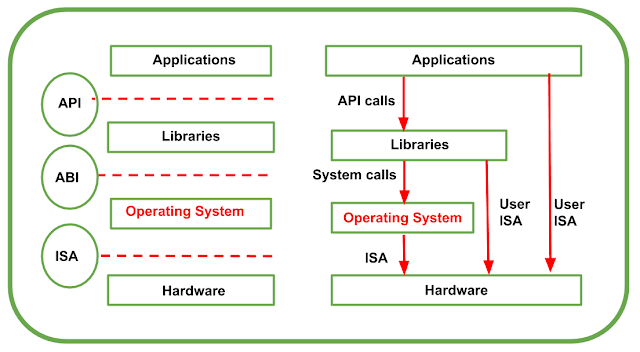
A Machine Reference Model
When an execution environment is virtualized at unlike levels of the stack of computation then it requires a reference model which defines the interfaces within the level of abstraction, and this level of abstraction hides the details of implementations. This projects an idea that virtualization techniques can substitute any one layer and can intercept the calls which are directed to it. That’s why a clear separation within the layers can simplify their implementations, which only need an emulation of the interfaces and a proper response with the underlying layer. At the base layer, the model for the hardware is declared or manifested in terms of architecture i.e. Instruction Set Architecture (ISA).
Instruction Set Architecture (ISA)
Instruction Set Architecture (ISA) defines the instruction set for the processor, registers, memory, and interrupt management. It is an interface between software and hardware and It is mandatory for the operating system (OS) developer (system ISA) developers of applications who directly manage core hardware (user ISA). The operating system layer is separated by the application binary interface (ABI) from the application and libraries, which are managed by the operating system.
Application Binary Interface (ABI)
Application Binary Interface (ABI) covers facts such as low-level data types and call conventions and it also defines a format for many programs. Mainly, system calls are defined at this level. Moreover, this type of interface enables the portability of various applications and libraries across OS which employ the same ABI. The application programming interface (API) is represented by the highest level of abstraction. This API interfaces applications to libraries and/or the core OS. Action is to be performed in the application level API, ABI, and the two which are responsible to make it done. Mainly, the CPU runs on two privilege levels:
1. User Mode: In this mode, memory access is restricted up to some limit whereas access to peripherals is denied.
2. Kernel Mode: In this mode, the CPU has instructions that manage memory and how to be accessed and it also has instructions that enable access to the peripherals like disks and network cards. From one running program to another running program, the CPU switches automatically. The expansions and packages of computing gadgets are simplified through this layered approach. The application of multitasking and co-lifestyles of more than one executing is simplified through this layered approach.
The first may be made inside privileged and non-privileged commands. Those commands which may be used with interrupting every other challenge are referred to as Non- privileged guidance. They also are referred to as so due to the fact that shared sources aren't accessed. Ex- consists of all of the constant points, floating, and mathematics commands. The commands that are performed beneath neath unique regulations and that are regularly used for touchy operations (which disclose behavior-touchy or regular manipulate touchily) are referred to as privileged commands.
It is anticipated that during hyper-visor-controlled surroundings, the code of visitor OS runs in consumer to save you it from the direct get admission to of OS’s status. It is not viable to absolutely isolate the visitor OS while non-privileged commands are implemented.
OR,
Machine Reference Model
- It defines the interfaces between the levels of abstractions, which hide implementation details. Virtualization techniques actually replace one of the layers and intercept the calls that are directed towards it.
- Hardware is expressed in terms of the Instruction Set Architecture (ISA).
– ISA for the processor, registers, memory, and interrupt management.
- Application Binary Interface (ABI) separates the OS layer from the application and libraries which are managed by the OS.
– System Calls defined
– Allows portabilities of applications and libraries across OS.
API – it interfaces applications to libraries and/or the underlying OS.
- The layered approach simplifies the development and implementation of a computing system.
ISA
ISA has been divided into two security classes:– Privileged Instructions – Nonprivileged Instructions
Nonprivileged instructions
- That can be used without interfering with other tasks because they do not access shared resources. Ex. Arithmetic, floating & fixed point.
Privileged instructions
- They are executed under specific restrictions and are mostly used for sensitive operations, which expose (behavior-sensitive) or modify (control sensitive) the privileged state.
– Behavior-sensitive = operate on the I/O
– Control-sensitive = alter the state of the CPU register.
Privileged Hierarchy:
Security Ring
- Ring-0 is in the most privileged level, used by the kernel.
- Ring-1 & 2 are used by the OS-level services and, R3 in the least privileged level is used by the user.
- The recent system supports two levels:
– Ring 3 = user mode




Comments
Post a Comment